A Timeline of Singapore and Spyware
What is Singapore's relationship to spyware? This timeline covers leaks and reports on surveillance tech firms previously linked to Singapore.
What is Singapore's relationship to spyware, or software which enables an actor to covertly obtain information from a device? Recent years have seen a drastic rise in news coverage on states' use of spyware, which has drawn controversy because of its use against not only national security threats, but also civilian targets such as activists and journalists.
Across these stories, a small but recurring thread is Singapore's presence in leaks and coverage of controversial spyware firms — from FinFisher to Hacking Team to Ability to QuaDream. This article compiles these instances in a single accessible timeline:
2013: Internet monitoring device used in Singapore
A 2013 Citizen Lab report revealed that Packetshaper was used in Singapore. Packetshaper is a device created by US-based company Blue Coat Systems that is capable of monitoring web traffic and filtering the internet.
2015: Singapore company listed as client of FinFisher

A Wikileaks release listed Singapore company PCS Security as a client of FinFisher. FinFisher is a German firm that sells spyware exploiting bugs in popular software such as iTunes or Microsoft Word to take control of or extract information from a target device.
Tech in Asia previously reported on PCS Security's government ties: "What makes it worse is when government agencies are the primary customers of that particular company." The Online Citizen reported that PCS Security was owned by another firm, the Phoenix Co-Operative Society, and pointed out that Phoenix was (at the time) one of two firms in Singapore that was given a very specific exemption under the Co-Operative Societies Act.
The Wikileaks release also alleged that using the software cost PCS Security at least 3,166,560 Euros (around 5.1 million SGD in 2012). The Wikileaks release also included support requests from PCS Security, including one which allegedly asked:
"I have a target which the computer is already infected with finspy. Would like to check is there any way which I could upload an executable to the target computer and then execute it?"
2015: Singapore listed as client of Hacking Team
In 2015, a Singapore government body (the Infocomm Development Agency) was listed as a customer in the leaked data of surveillance tech company Hacking Team. This Italy-based firm marketed itself as providing "effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities" — but a Citizen Lab report points to links between Hacking Team and the government agencies of 21 mostly non-democratic or authoritarian states.
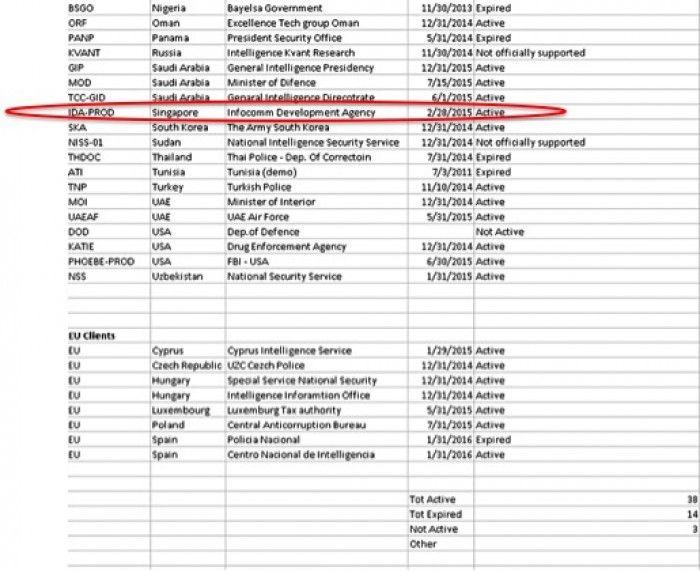
Screenshots from the leak allege that Singapore's InfoComm Development Agency (IDA) was an "active" client. Hacking Team's now-defunct website stated:
"It doesn’t matter if you are after an Android phone or a Windows computer: you can monitor all the devices. Remote Control System is invisible to the user, evades antivirus and firewalls, and doesn’t affect the devices’ performance or battery life. Hack into your targets with the most advanced infection vectors available. Enter his wireless network and tackle tactical operations with ad-hoc equipment designed to operate while on the move."
Professor Eugene Tan of Singapore Management University gave this comment as part of a story by Digital Media Asia after the leak:
"I would say that we are in a state of affairs in which very little is known about what the Government conducts surveillance on, how it does it, and the regulatory controls in place."
2017: Singapore reportedly a client of Ability Inc.
In 2017, Ability Inc, an Israeli surveillance company specialising in cellphone snooping technologies, faced a leak and lawsuits over its misconduct. What was Ability selling? According to the Forbes report on this leak:
Sales data handed to Forbes, dated 2015-2016, shows shipments of a variety of spy tools, including its Touchdown tech for intercepting and decrypting 3G cellphone communications and its In-Between Interception System (IBIS) product for 2G. The 3GCat, meanwhile, would downgrade connections from 3G to 2G, the latter having weaker security protections and therefore easier to snoop on.
According to Forbes, clients in Singapore spent 5 to 7.5 million USD on Ability's technology. While Forbes was unable to confirm which government agency was behind the purchase, Ability reportedly only sold its technology to law enforcement and intelligence agencies.
2018: Pegasus and the NSO Group
A 2018 Citizen Lab analysis found suspected Pegasus spyware infections in 45 countries, including Singapore. The Israeli spyware firm behind Pegasus, NSO Group, became subject to intense media scrutiny in 2021, after revelations that Pegasus was used against journalists, activists and politicians by government agencies across the globe.
Pegasus is noteworthy for its "zero-click" attacks, which can infect a phone device without interaction from its user. After infection, Pegasus can extract information such as email and calendar data, record phone calls, and activate the phone's camera. According to the Guardian's explainer on Pegasus:
One of the most significant challenges that Pegasus presents to journalists and human rights defenders is the fact that the software exploits undiscovered vulnerabilities, meaning even the most security-conscious mobile phone user cannot prevent an attack.
“This is a question that gets asked to me pretty much every time we do forensics with somebody: ‘What can I do to stop this happening again?’” said Guarnieri. “The real honest answer is nothing.”
2021: Singapore user(s) targeted by Candiru
A 2021 Citizen Lab analysis exposed Candiru, another Israeli mercenary spyware firm, which exploited security vulnerabilities in Windows. A Microsoft investigation found over 100 victims of Candiru, and identified at least one victim located in Singapore.
2021: Singapore firm COSEINC blacklisted by US
A Singapore-based cybersecurity firm, COSEINC, was blacklisted by the US in 2021. COSEINC was blacklisted alongside high-profile firms that have drawn intense controversy over their surveillance of politicians, journalists and activists, such as Pegasus and Candiru.
According to their website, COSEINC is a "Singapore based and privately funded company dedicated to providing highly specialized information security services to our clients. Founded in 2004, we are a young and dynamic company made up of computer security experts, from diverse backgrounds and geographies, with distinguished credentials and experience." Their website lists an Advanced Malware Lab and Vulnerability Research Lab.
Since the blacklisting, the Cyber Security Agency of Singapore has stated that it is "looking into the matter." COSEINC's webpages from 2020 (found on the internet archive) indicate that COSEINC was active in organising activities that were "driven by" Singapore's Infocomm Media Development Authority (IMDA):
Edit: According to information from the government procurement platform, COSEINC was awarded a SGD 184,067.59 contract for "Provision of Accredited Cybersecurity Training and Certification" by Singapore's Ministry of Defence in 2018.
2021: Singapore journalists potentially targeted by cyber mercenaries
In December 2021, Facebook suspended around 1,500 fake accounts used by 7 surveillance-for-hire firms to target users on their platform. As part of this move to ban these cyber mercenaries on their platform, they also informed nearly 50,000 Facebook users who have potentially been targeted by these groups.
Singapore journalists Kirsten Han and Terry Xu shared on social media that they received a security notice from Facebook, warning them "that a sophisticated attacker may be targeting your Facebook account."

The 7 banned firms are located in Israel, India, North Macedonia and China, and sold their services to more than two dozen countries. According to Facebook and the Citizen Lab, these firms have previously targeted prominent activists and human rights defenders, and had even been used on behalf of Hollywood rapist Harvey Weinstein.
2022: Singapore reportedly a client of spyware firm QuaDream
A Reuters investigation found that another spyware firm had been exploiting the same flaw in Apple's software used by NSO Group's Pegasus spyware. The firm, QuaDream, is a smaller Israeli firm that also develops hacking tools intended for government clients. According to Reuters:
One of QuaDream's first clients was the Singaporean government, two of the sources said, and documentation reviewed by Reuters shows the company's surveillance technology was pitched to the Indonesian government as well. Reuters couldn't determine if Indonesia became a client.
Curiously, the Straits Times' print coverage of this story excluded this mention of Singapore. The online article still retains this passage, however.
Beyond spyware as surveillance
While the threat of spyware is drawing the greatest amount of public attention, one should not overlook other forms of surveillance, which can be far more pervasive and normalised. These examples can be seen in nearly all walks of life in Singapore:
Monitoring students: Singapore's Ministry of Education plans to require monitoring software on students' laptops, capturing students' search data to target "objectionable content" and allowing teachers to remotely monitor and control these devices. A student-led petition against this decision asks:
Will the [Device Management Application] help students become more mature? Will it bring about lasting behavioral benefits? Will it solve the root of the problem in the long term? Or will it bring about temporary, superficial, short term consent, at the cost of a permanent opinion malus, a hatred of authority, and a loss of privacy? Does [the Ministry of Education] not strive to build a values-based education?

Monitoring migrant workers: Migrant workers in Singapore have been subject to intense surveillance in the wake of the COVID-19 pandemic, via apps (the SGWorkPass app, on top of the TraceTogether app used by most citizens) and via patrolling robots. These tools are used to police everything from their recreation time to whether they are allowed to leave their dorms. According to Rest of World, the robots used to surveil migrant workers "got out of the dormitories before the migrant workers did," when similar robots were deployed to patrol a residential district while migrant workers continued to face repressive lockdowns.
Monitoring public spaces: Singapore's Minister of Home Affairs has announced plans to double the number of security cameras in Singapore to over 200,000 by 2030. Compared to other cities, this would place Singapore within the list of most surveilled cities in the world. These figures do not include other forms of public surveillance, like Singapore's planned rollout of "smart street lamps" intended to detect speeding e-scooters and predict "unruly crowds."

Monitoring prisons: Singapore's prison system is now making greater use of video analytics and facial recognition in its surveillance of prisoners. Channel News Asia's recent documentary series on life in Singapore's prisons also shows some of the extent of the surveillance that prisoners in maximum security live with.

Monitoring everything? After the United States' controversial Total Information Awareness (TIA) surveillance project fell out of favour under public and congressional scrutiny in 2003 for seeking to impose mass surveillance on American citizens, it inspired a more all-encompassing and centralised surveillance project in Singapore. One of its architects, John Poindexter, even consulted on this Singapore project, which became known as the Risk Assessment and Horizon Scanning (RAHS) program.
RAHS was launched in 2004 and analyses a wide range of sources (which the government does not disclose) for indicators of potential threats, by combining big data with hypothetical narratives constructed by analysts. Foreign Policy reported that the government has acknowledged that publicly available information (such as social media content) is monitored.
The exact boundaries of cyber surveillance in Singapore, from both the state and other sources, remain unclear. The lack of laws to protect privacy ensures that this is likely to remain the status quo, with few options for those demanding transparency or accountability over the growing surveillance in their lives.
Adding to this Timeline
Have a tip or suggestion? Contact Singapore Samizdat via teokaixiang@protonmail.com.
Corrections: The article initially stated that "a client in Singapore spent 7.5 million USD on Ability's technology." This was an error, and has been amended to "clients in Singapore spent 5 to 7.5 million USD on Ability's technology."






We are now 3 years into the future and the SG government never fails to strike again.
https://citizenlab.ca/2025/03/a-first-look-at-paragons-proliferating-spyware-operations/
This news is from 19 Mar 2025, a day ago dated from this post, and Singapore is once more on the buyers list of Israel's newest surveillance tech Paragon.